The second byte in the IPv4 header (aka “those bits you’ve probably never, ever looked at”) is used for Differentiated Services, or DiffServ. It’s split into two parts: the 6 most significant bits define the DSCP (differentiated services code point) and the two least significant bits are for ECN (explicit congestion notification). You can use DSCP to divide your traffic into different classes. For example, Asterisk might use the following DiffServ value, which corresponds EF (Expedited Forwarding):
DSCP ECN 10111000
If your networking equipment is sufficiently aware, this traffic will receive preferential treatment.
You can filter these values pretty easily using the ip.dsfield.dscp display filter — just right-click on the DSCP field in the packet like so:
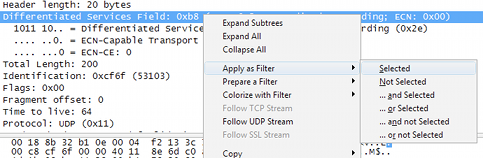
Applying a DSCP display filter
What if you need to use DSCP in a capture filter?
To match against a particular DSCP codepoint using BPF (WinPcap/libpcap’s filtering language) you need to take the bit pattern, left-shift it two places to account for the ECN, and mask out the ECN. For EF (101110) you’d have do something like this:
- Take 101110 and shift it left two bits: 10111000
- Convert it to hex: 0xb8
- Create a filter, masking out the ECN bits:
ip[1] & 0xfc == 0xb8
Cisco has a list of code points at http://www.cisco.com/en/US/tech/tk543/tk757/technologies_tech_note09186a00800949f2.shtml
P.S. To make matters more confusing, the DiffServ field was originally called “Type of Service.”