For over 25 years, network professionals have relied on Wireshark packet captures (pcaps) to analyze and troubleshoot network system behavior. But packets are scarce in the cloud. Is it possible to get the same level of visibility and granularity there? And if so, is there an opportunity to leverage the same principles that have made Wireshark so ubiquitous?
Well, the answer to both questions is yes. We’ve named this new tool Stratoshark, and it’s powered by system calls.
One of the things that has contributed to Wireshark’s success is that it is part of the pcap ecosystem, which is centered around libpcap and the pcap and pcapng file formats. It all started with tcpdump, and over time other tools appeared. The ecosystem now includes Zeek (formerly Bro), Snort, WinPcap, nmap, nTop, Kismet, Suricata, and many others.
Each tool focuses on its specific job but together form a collective powerhouse. A common file format means that you can pivot between each tool with little to no effort. For example, you can take a capture file from Zeek or Snort and load it into Wireshark for detailed analysis. If you take a step back and look at the ecosystem as a whole, you might wonder if that same effectiveness and success can be applied elsewhere. As it turns out, with system calls, it can.
If you’re not familiar with system calls (this is a networking blog, after all), they can be thought of as a boundary between your operating system and all of the applications running on your system. Any time an application wants to do something useful, such as opening a file, connecting to the Internet, or playing a sound, it uses system calls. This is true whether you’re running on Windows, macOS, Linux, or any other OS. System calls can also be used to enforce security boundaries. For example, if an application tries to read or write a file that it shouldn’t, the operating system can say “no.”
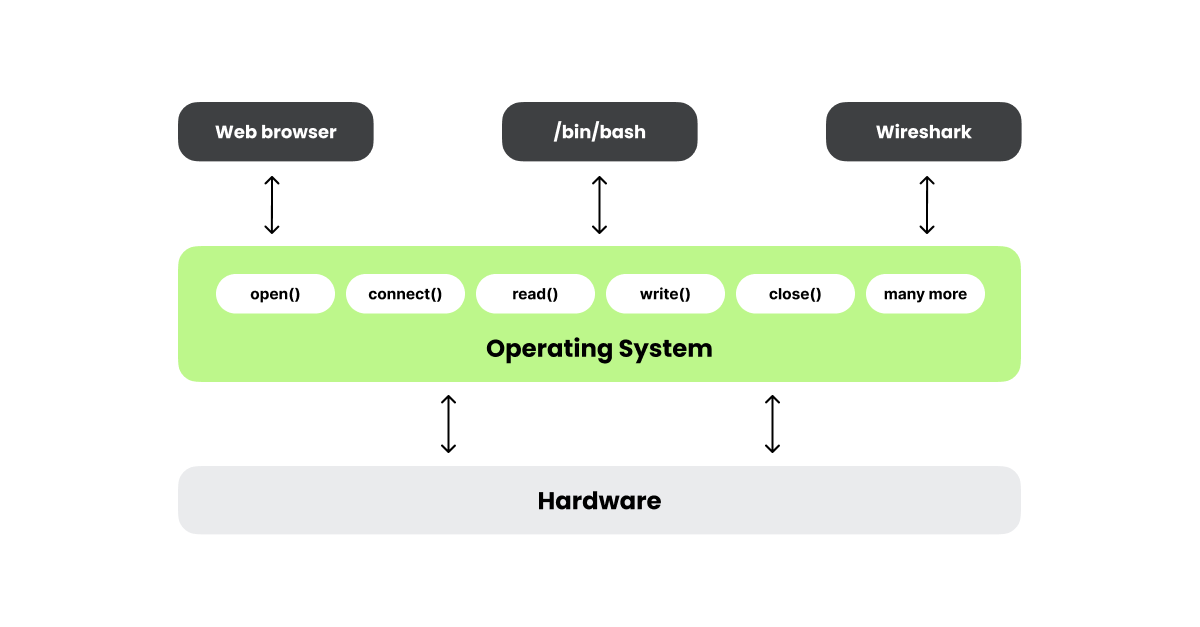
If you can tap into that boundary and see what system calls each application is using you can get an excellent view into your system’s behavior. This is what tools like Falco and Sysdig OSS do. Sysdig OSS is a command line tool that works much like tcpdump, and prints system call activity on your terminal screen. Falco works much like an IDS, constantly monitors syscall activity, sending alerts whenever it finds something suspicious. Falco and Sysdig OSS are part of the scap (system capture) ecosystem. This ecosystem is based around the libscap library, which can capture system calls and read and write .scap files, and libsinsp, which enriches the information captured by libscap by adding information such as usernames and file paths. Libscap also has a plugin interface that lets you capture from other sources, such as cloud providers and application logs.
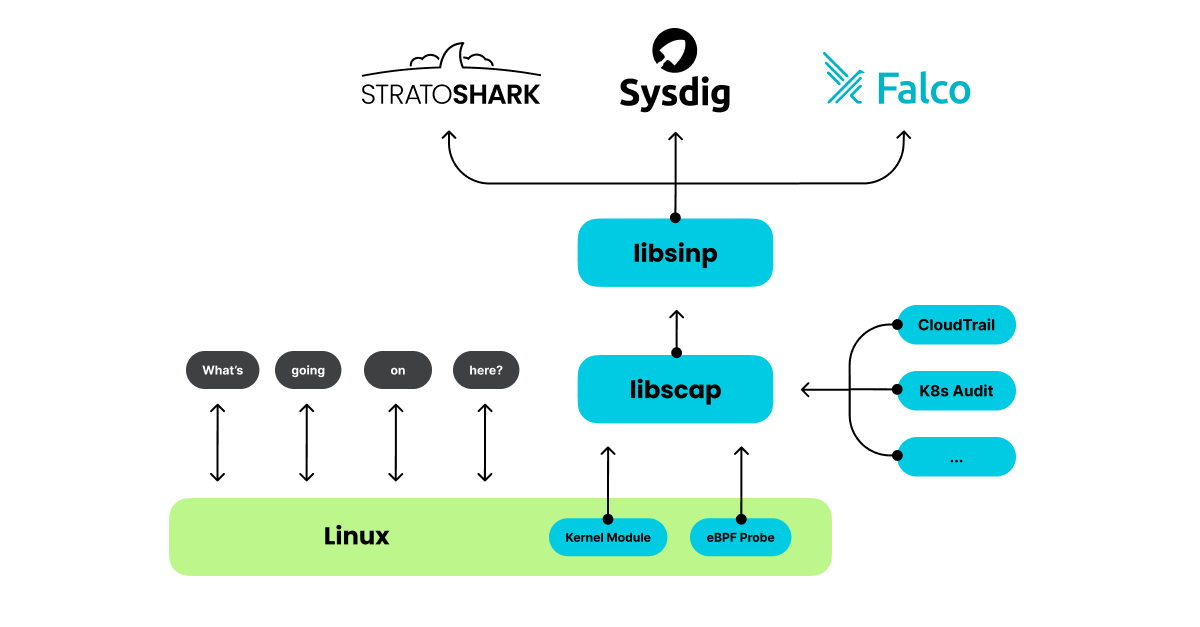
What if we took the powerful analysis features of Wireshark and made it possible to analyze the system call and log data provided by libscap and libsinsp? I’m thrilled to announce that we did that, and it’s called Stratoshark.
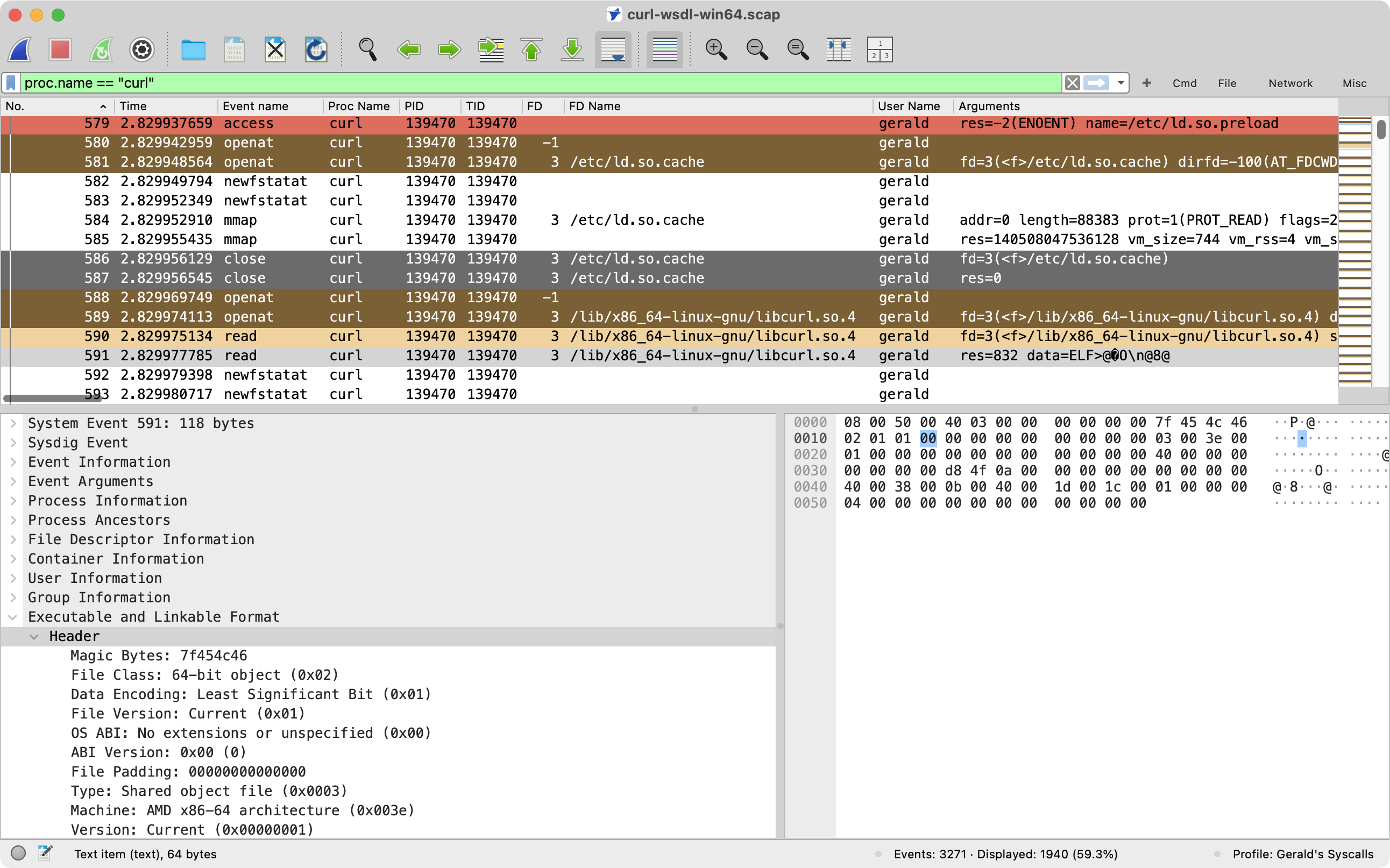
Stratoshark is a sibling application to Wireshark that lets you analyze system calls and logs. If you look closely at the screenshot below, it should look familiar to anyone who’s used Wireshark. However, the first thing you might notice is that those aren’t packets. In this case, they’re a capture of the curl utility downloading a file. If you scroll through the event list you can see the various system calls that it uses to get up and running, from loading its dynamic libraries to reading certificate files to connecting to the remote server. You can see the process name, user name, file paths, and other useful information. In this particular instance, I’ve selected an event that reads a dynamic library. After dissecting the system call, Stratoshark proceeds further and dissects the executable header in the library file itself.
I’m really excited about Stratoshark because it lets you peer into the inner workings of systems in the same way that Wireshark lets you peer into the inner workings of networks. I hope that you find it useful, and I’m looking forward to seeing how Stratoshark grows and evolves as part of the scap ecosystem.
You can download Stratoshark for Windows and macOS and find a link to its source code at stratoshark.org. If you’d like to learn more you can find information at the following locations.
Stratoshark: Extending Wireshark’s legacy into the cloud on the Sysdig blog
How Falco and Wireshark paved the way for Stratoshark on the Sysdig blog
Getting Started With Stratoshark on Josh Clark’s blog
How to capture an SCAP for Stratoshark on Medium
Stratoshark on the Wireshark wiki