Wireshark’s Welcome Screen
Wireshark 1.2 added a nifty welcome screen which lets you start capturing, load a capture file, get help, and lots of other things. At the very top of the screen we brag about our popularity.
You can change that message to anything you like.
🔗
More Shark Pictures
Filtering DSCP
The second byte in the IPv4 header (aka “those bits you’ve probably never, ever looked at”) is used for Differentiated Services, or DiffServ. It’s split into two parts: the 6 most significant bits define the DSCP (differentiated services code point) and the two least significant bits are for ECN (explicit congestion notification). You can use DSCP to divide your traffic into different classes. For example, Asterisk might use the following DiffServ value, which corresponds EF (Expedited Forwarding):
DSCP ECN 10111000
If your networking equipment is sufficiently aware, this traffic will receive preferential treatment.
You can filter these values pretty easily using the ip.dsfield.dscp display filter — just right-click on the DSCP field in the packet like so:
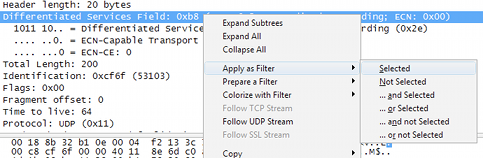
Applying a DSCP display filter
What if you need to use DSCP in a capture filter?
Recent Posts
- Those Aren't Packets: How Stratoshark Brings the Power of Wireshark to the Cloud
- What’s New In Wireshark 4.4?
- From Network Packets to Log Data: How Logray built upon Falco’s foundation
- The evolution of system introspection from BPF to Wireshark to Falco
- Wireshark Is 25: The email that started it all and the lessons learned along the way